
Solutions
Network and Vulnerability Management
Intrust
Event Log Management for Security and Compliance
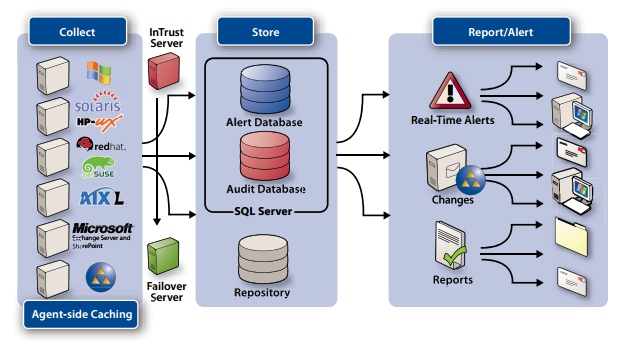
InTrust securely collects, stores, reports and alerts onevent log data from Windows, Unix and Linux systems, helping you comply with external regulations, internal policies and security best practices. InTrust helps you achieve regulatory compliance by auditing user access to critical systems and detecting inappropriate or suspicious access-related events. With this tool, you can collect, analyze, report and generate automated real-time alerts for all relevant access-related events across your heterogeneous network.
Using this single solution to monitor access to critical systems on multiple platforms reduces the complexity of event log management, saves storage administration costs, improves information assurance, mitigates risk and helps to reduce cost and improve efficiency of security, operational and compliance reporting.
Features:
- Key to Compliance: Addresses regulatory compliance by collecting and reporting on event logs across the entire IT stack, monitoring user access to critical systems and applications and allowing you to perform forensic analysis of user and system activity based on historical event data.
- User Activity Tracking: Collects events on user and administrator activity from diverse and spread-out systems and applications and presents them in an easy-to-use and complete form suitable for ongoing reporting and ad hoc analysis. Extracts all the essential details of user access such as who performed the action, what that action actually entailed, which server it happened on and which user workstation it originated from.
- Automated Log Collection: Automates the secure collection of event logs, decreasing your workload.
- Log Data Compression: Provides unparalleled long-term compression, versus storing the same amount of event data in a database.
- Log Integrity: Enables you to create a cached location on each remote server where logs can be duplicated as they are created, preventing a rogue user or administrator from tampering with the audit log evidence.
- Forensic Analysis: Provides tools for interactive searching through historical event log data for on-the-spot investigation of security incidents and policy violations and preparation of evidence suitable for submission to the court.
- Real-Time Alerting: Sends real-time alert notifications about unauthorized or suspicious user activity directly to you via email or to third-party monitoring applications such as Microsoft Operations Manager (MOM).
- Flexible Reporting: Gives you unprecedented access to predefined and customizable reports, supporting a wide variety of file formats, including HTML, XML, PDF, CSV and TXT, as well as Microsoft Word, Visio and Excel.
- Fault Tolerance: Provides automated server redundancy in the case of failure, enabling you to quickly move all configurations and jobs from a crashed server to a backup server to handle all activity and reducing the possibility of lost log files due to server failure.
-
Datasheet
- Cybersecurity Solutions
- InTrust
- InTrust for Workstations
- 10 Best Practices for Reducing the Stress of IT Audits
- Best Practices Guide for IT Governance & Compliance
- Better Together: Auditing with Microsoft Audit Collection Services & Quest Software
- Azaleos Chooses Quest Service Provider Partner Program to Offer Fully Managed, Secure and Compliant Exchange 2010 Environments
- InTrust Exceeds BRFkredit’s Compliance Needs
- InTrust Offers Compliance and Security Indemnity for Ohio Department of Insurance
- Large Catholic Health Care Provider Finds Cure to Efficient System Security at Quest
- Pentagon Heightens Security with InTrust
White Papers
Case Studies
For more information about InTrust,
please contact our Sales Representative at 2556 2162, or email at sales@ppn.com.hk.
Copyright © 2021 Pacific Professional Network. All rights reserved.
